Two Factor Authentication mit RSA, SafeWord oder einer beliebigen RADIUS Lösung ist eine gängige Methode zur sicheren Authentifizierung an einem AAC Deployment. AAC beschriftet das Eingabefeld für das RSA/SafeWord/RADIUS One Time Passwort bei einem deutschen Client jedoch starr mit dem Text “SecurID-PASSCODE”, “SafeWord CODE:” oder generisch mit “RADIUS-Passwort”.
Endbenutzer kennen ihre One Time Passwort Lösung jedoch meist unter einem anderem Namen, meist dem Namen des Herstellers. Dies kann dann zu Verwirrung und Problemen bei der Eingabe führen.
Dieses Problem lässt sich für RSA und SafeWord recht einfach lösen. Eine Lösung für RADIUS ist weiter unten beschrieben. Wie schon im ersten und zweiten Beitrag zu dieser Reihe, befindet sich der Schlüssel in der Datei “web.config” im Root des jeweiligen LogonPoint Verzeichnisses.
Auf einem Standard AAC Server vermutlich unter:
C:\Inetpub\wwwroot\CitrixLogonPoint\#LogonPointName#
Es existiert noch eine weitere Version dieser Datei unter “C:\Inetpub\wwwroot\CitrixLogonPoint\”, welche unberührt bleiben sollte !
Diese Datei lässt sich mit einem Editor wie z. B. NotePad öffnen und bearbeiten. Im letzten Drittel findet sich der Abschnitt <appSettings>, in dem diverse Einstellungen vorgenommen werden können. Unter Anderem lässt sich hier auch die Anzeige für das Eingabefeld des One Time Passwords manipulieren, so dass ein beliebiger Text angezeigt werden kann. Dazu genügt es, folgende Zeilen im <appSettings> Block einzufügen:
<add key=”SecondaryAuthenticationPromptOverride” value=”Password:” />
und
<add key=”SecondaryAuthenticationToolTipOverride” value=”Enter Password” />
Wobei “Password:” für den anzuzeigenden Text steht und “Enter Password” den Text für den Tool Tip festlegt.
Der Abschnitt sollte dann z. B. so aussehen:
<appSettings>
<add key="DebugConsoleTrace" value="False" />
<add key="AdvancedGatewayClientDownloadUrl" value="http://www.citrix.com" />
<add key="AdvancedGatewayClientActivationDelay" value="10" />
<add key="MaxConnectionsToAuthenticationService" value="20" />
<add key="LogonPointId" value="00000000-0000-0000-0000-000000000000" />
<add key="DeployedBy" value="LACONFIG" />
<add key="ExtendedSecurIdFunctionalityEnabled" value="true" />
<add key="SecondaryAuthenticationPromptOverride" value="SafeWord PIN + Zahlencode:" />
<add key="SecondaryAuthenticationToolTipOverride" value="PIN und Zahlencode eingeben" />
<!- -
Nach dem Speichern der Datei und einem Refresh des LogonPoints sollte der neue Text erscheinen 🙂
Dieses Vorgehen funktioniert leider nur bei RSA SecureID und SafeWord. Der Text, welcher bei einer RADIUS Lösung angezeigt wird, ist leider hart codiert und kann nicht so einfach geändert werden. Es gibt zwar bereits einen Feature Request bei Citrix, aber wann eine Lösung effektiv verfügbar sein wird, ist momentan noch nicht abzusehen.
Joel Donaldson hat im Citrix AAC Forum jedoch auch für diesen Fall eine tolle Umgehungs- / Übergangslösung veröffentlicht. Eine einfache Manipulation der Datei BasePage.aspx aus dem jeweiligen LogonPoint Verzeichnis läst das Problem auf elegante Art und Weise.
Es genügt, bei einem deutschen LogonPoint, folgenden Abschnitt vor dem </body> Tag einzufügen:
<script type="text/javascript" language="JavaScript">
document.body.innerHTML=document.body.innerHTML.replace("RADIUS-Kennwort:","Kobil Einmalpasswort:");
</script>
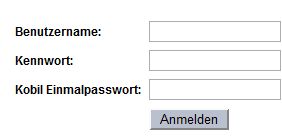
Das Ergbnis sieht dann so aus:
Sollen auch englische LogonPoints unterstützt werden, hilft ein weiterer Code Block, der die englische Schreibweise berücksichtigt:
<script type="text/javascript" language="JavaScript">
document.body.innerHTML=document.body.innerHTML.replace("RADIUS Password:","Kobil OTP:");
</script>
Weitere Sprachen können so leicht hinzugefügt werden.
Wer sich nun fragt, warum das funktioniert, dem kann evtl. diese Erklärung weiterhelfen. Der Script Code sucht im Text der ausgelieferten Webseite nach dem String “RADIUS-Kennwort:” und ersetzt ihn dann durch den zweiten Parameter der Funktion “document.body.innerHTML.replace”, also in unserem Beispiel durch “Kobil Einmalpasswort:”.
Achtung, dies funktioniert nur, solange JavaScript im Browser aktiviert und erlaubt ist. Ist JavaScript abgeschaltet, erscheint wieder der ursprüngliche Text “RADIUS-Kennwort:”! Weitere Nebenwirkungen sind bei dieser Anpassung nicht zu befürchten.
< < AAC Tuning, Teil 2
!!! Bitte beachtet den ersten Kommentar zu diesem Beitrag !!!
Gruss
Ecki
Two Factor Authentication with RSA, SafeWord or any other third party RADIUS solution is a common way to authenticate in a secure manner to an AAC deployment. AAC however labels the input box for the OTP (One Time Password) fix with the text “SecurID-PASSCODE”, “SafeWord CODE:” oder generic with “RADIUS Password”.
Endusers however know their OTP solution most of the time with other names, the name of the RADIUS solution provider for example. This can lead to confusion during the login process.
This problem is easily solved for RSA SecureID and SafeWord. A solution for RADIUS is described further down. As in part 1 and 2, the solution can be found in the “web.config” file in the root of the respective LogonPoint directory.
On a standard AAC server this is presumably:
C:\Inetpub\wwwroot\CitrixLogonPoint\#LogonPointName#
There is an other version of this file in the “C:\Inetpub\wwwroot\CitrixLogonPoint\” directory which should stay untouched !
This file can be opened and edited with any editor like the Windows NotePad. In the last third of the file you can find a section <appSettings>, which gives you some interesting possibilities. Among other things you can configure the lables for the OTP field, so that it displays a text your users expect. All it needs, is to change the following line below the <appSettings> section:
<add key=”SecondaryAuthenticationPromptOverride” value=”Password:” />
and
<add key=”SecondaryAuthenticationToolTipOverride” value=”Enter Password” />
Where “Password:” stands for the text to be displayed as lable and “Enter Password” stands for the text, displayed as tool tip.
The section should look like this afterwards:
<appSettings>
<add key="DebugConsoleTrace" value="False" />
<add key="AdvancedGatewayClientDownloadUrl" value="http://www.citrix.com" />
<add key="AdvancedGatewayClientActivationDelay" value="10" />
<add key="MaxConnectionsToAuthenticationService" value="20" />
<add key="LogonPointId" value="00000000-0000-0000-0000-000000000000" />
<add key="DeployedBy" value="LACONFIG" />
<add key="ExtendedSecurIdFunctionalityEnabled" value="true" />
<add key="SecondaryAuthenticationPromptOverride" value="SafeWord PIN + Zahlencode:" />
<add key="SecondaryAuthenticationToolTipOverride" value="PIN und Zahlencode eingeben" />
<!- -
After saving the changes, a user calling this manipulated LogonPoint should now see the new lable.
This method unfortunately works only for RSA SecureID and SafeWord. The text displayed, when using a third party RADIUS solution is hard coded and not that easy to manipulate. There is a pending feature request at Citrix, but it isn’t clear, when a solution will be publicly available.
At last I found a very good work-around in the Citrix AAC Forum, published by Joel Donaldson. A simple manipulation of the BasePage.aspx file of the respective LogonPoint solves the problem in an elegant way.
With an english LogonPoint it is sufficient, to add the following paragraph before the </body> tag:
<script type="text/javascript" language="JavaScript">
document.body.innerHTML=document.body.innerHTML.replace("RADIUS Password:","Kobil Einmalpasswort:");
</script>
The result will look like this:

If you want to support german LogonPoints also, you need another code block that respects the german notation:
<script type="text/javascript" language="JavaScript">
document.body.innerHTML=document.body.innerHTML.replace("RADIUS-Kennwort:","Kobil Einmalpasswort:");
</script>
Other languages can be added easily this way.
If someone is asking itself why this works, this short explanation may help. The script code is looking for the string “RADIUS Password:” in the delivered web page and replaces it with the second parameter of the function “document.body.innerHTML.replace”, in our example “Kobil OTP:”.
Attention, this works only, if JavaScript is enabled in the browser. If JavaScript is disabled, the original text “RADIUS Password:” is displayed. This modification shouldn’t have any other side effects.
< < AAC tuning, part 2
!!! Please read the first comment to this post !!!
Regards
Ecki